Asset Management
Atomic Enterprise OSSEC (AEO) supports centralized Asset Managent for Agent and Agentless devices.
Overview
File Integrity Monitoring
Anti-Virus
Log Monitoring
Scheduled Tasks (Scanning, and Reporting)
1.0 File Integrity Monitoring (FIM)
FIM settings are configurable by host platform (Linux or Windows) and includes a default policy suitable for generic configurations
1.1 Global Settings
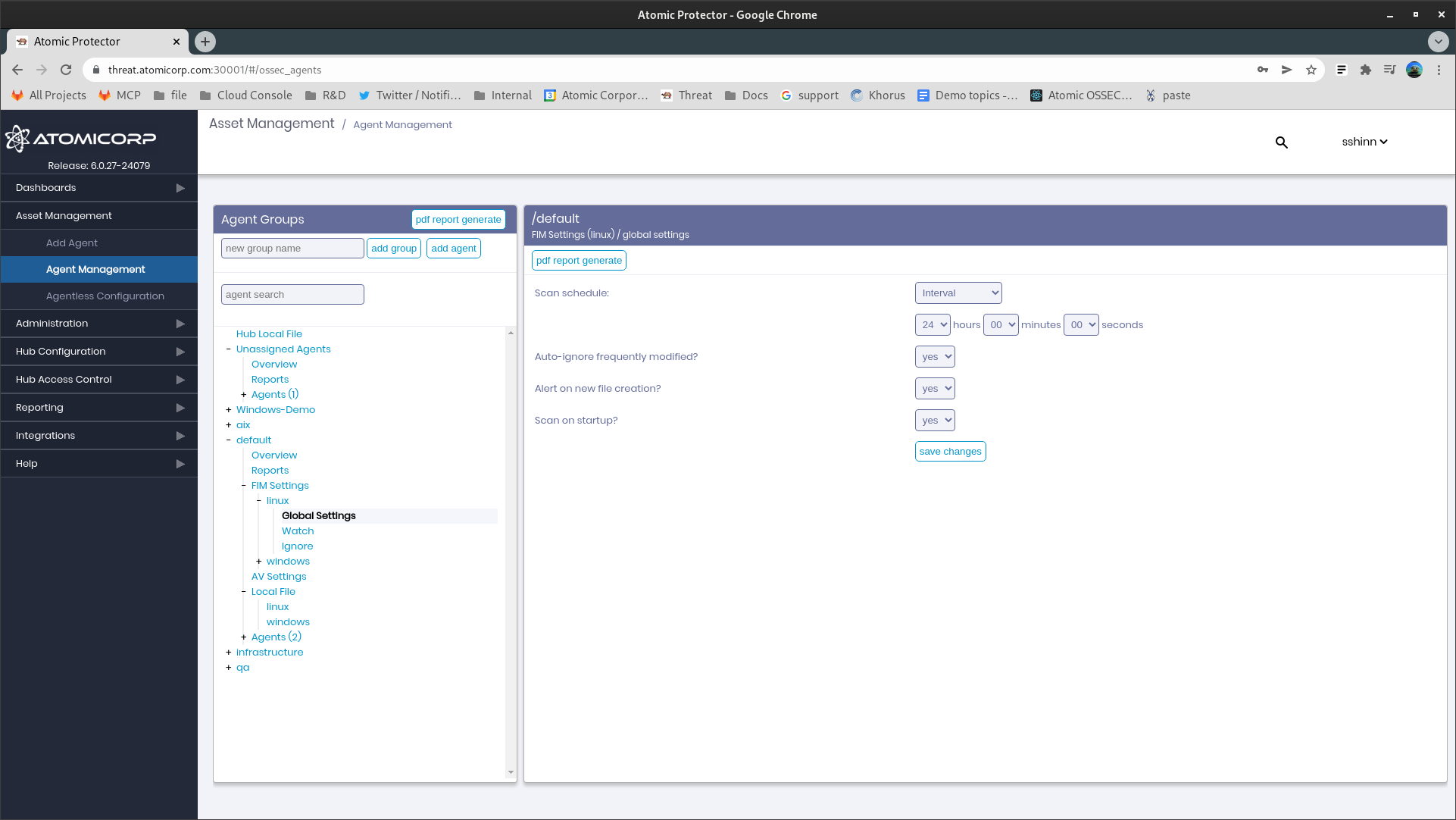
1.1.1 Scan Schedule
Declare time and/or day of the week to run static scans. Generally this is used for environments that do not support real-time FIM
1.1.2 Auto-Ignore Frequently Modified
Automatically do not report changes to a file that changes 3 times in succession
1.1.3 Alert on new file creation
Alert when new files are added to the system
1.1.4 Scan on startup
Run a FIM scan when the agent starts
1.2 Watch
Note
Default Windows and Linux profiles are included
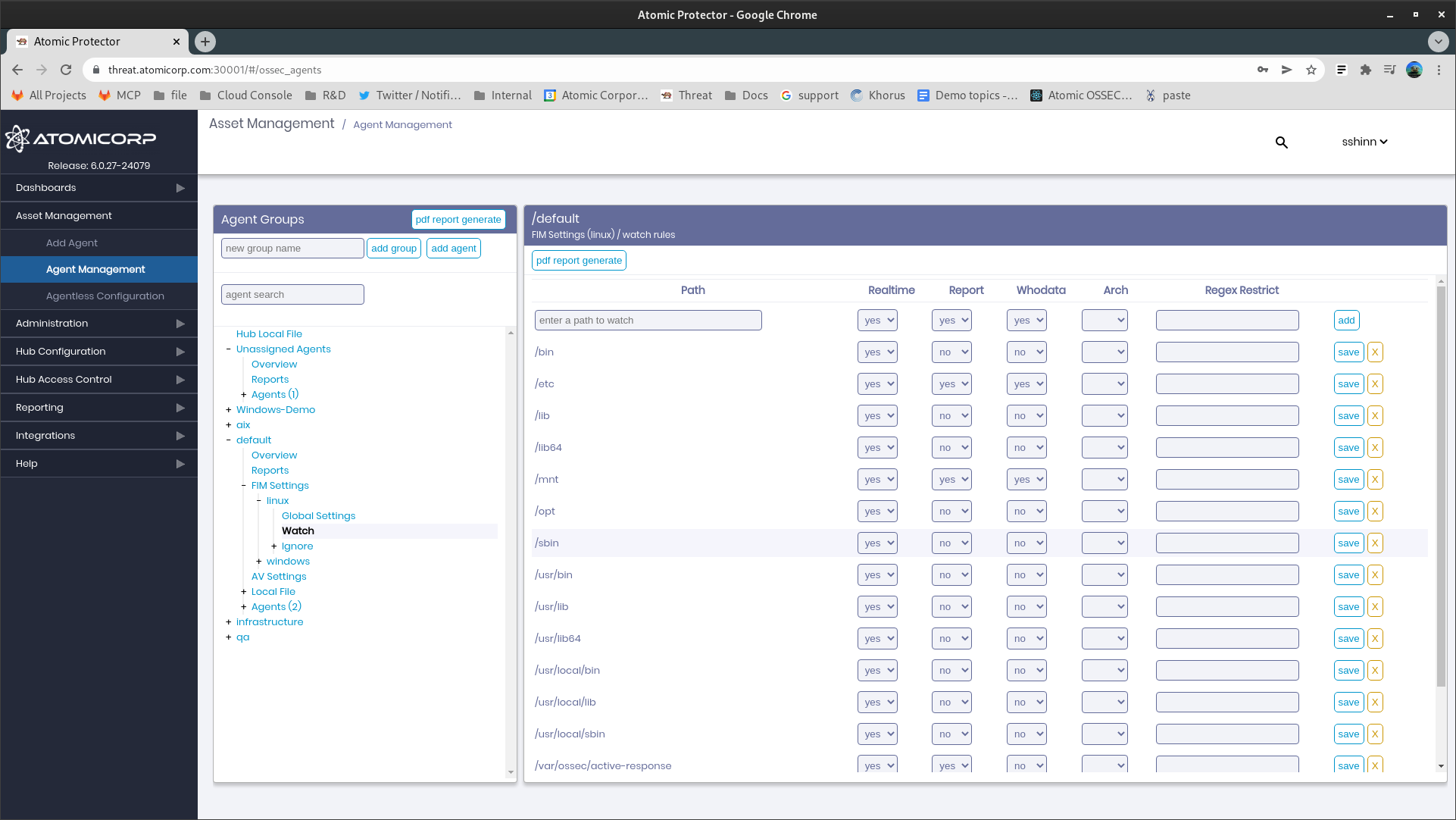
1.2.1 Path
Path of the file, or registry key to monitor.
Note
When declaring paths, always use unix style /. Example: C:/exampledirectory
1.2.2 Realtime
Enable realtime detection of changes.
Note
This is safe to enable even if the (legacy) environment does not support real-time detection
1.2.3 Report
Track changes to files made in the enviroment. ASCII file deltas are included in the alert. Files are maintained on the agent in a revisioned directory under /var/ossec/queue/diff or C:/Program Files (x86)/ossec-agent/queue/diff/
Note
This can increase disk space usage
1.2.4 Whodata
Include information on the user that made the change. This option is supported on all modern operating systems
1.2.5 Arch
(Windows Only) Used to limit registry settings to a specific architecture, i386 or x86_64. This option defaults to checking both
1.2.6 Regex restrict
Limit FIM to simple regular expressions. Example: .js$|.css$|.html$
^ -> To specify the beginning of the text. $ -> To specify the end of the text. | -> To create an "OR" between multiple patterns.
1.3 Ignore
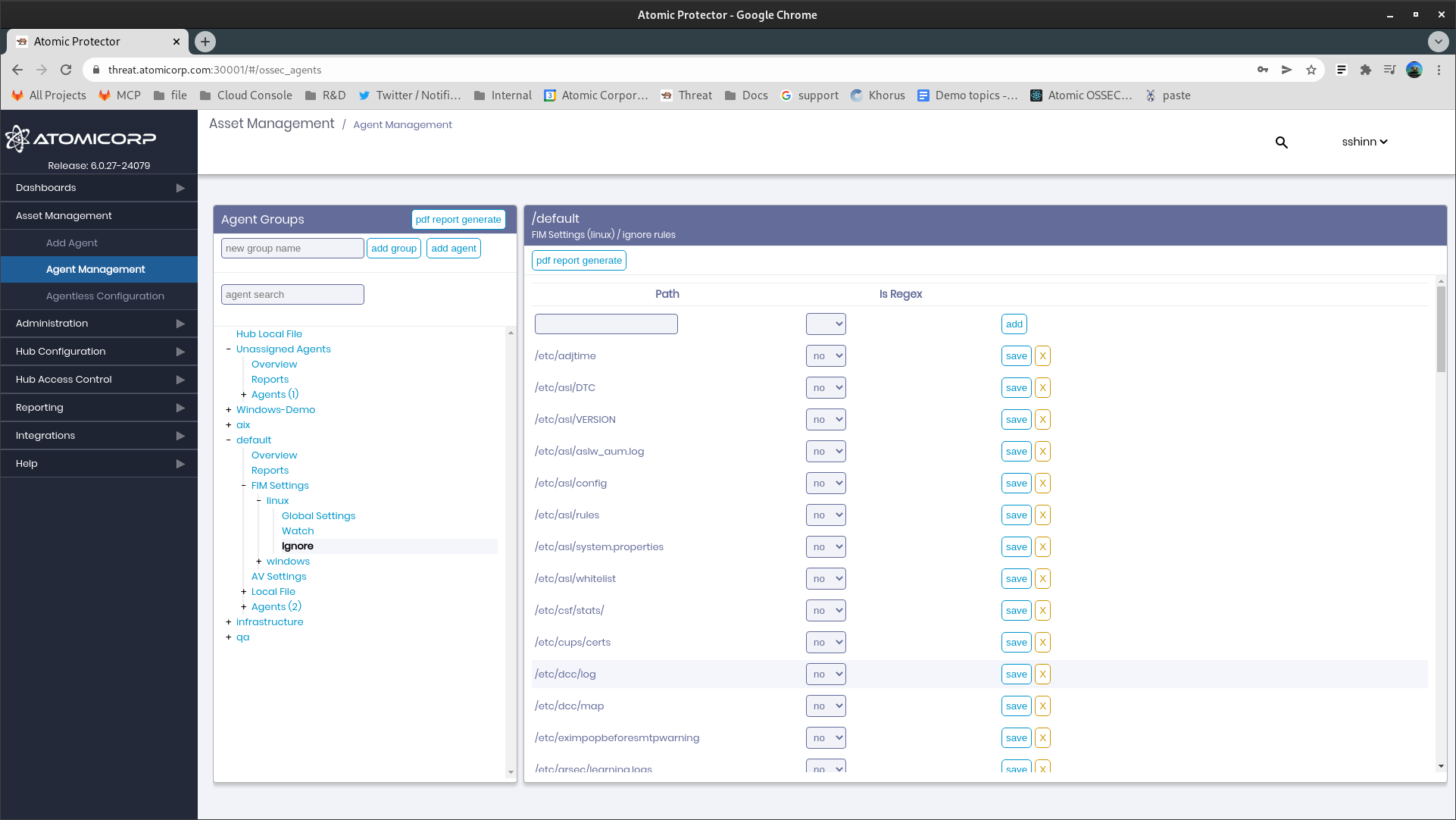
1.3.1 Path
Path or simple regular expression to ignore.
^ -> To specify the beginning of the text. $ -> To specify the end of the text. | -> To create an "OR" between multiple patterns.Note
Globbing is not supported at this time
1.3.2 Is Regex
Toggle the field used in Path is a simple regular expression
2.0 Log File Monitoring
AEO can perform IDS monitoring of Log files, windows eventchannels, or processes.
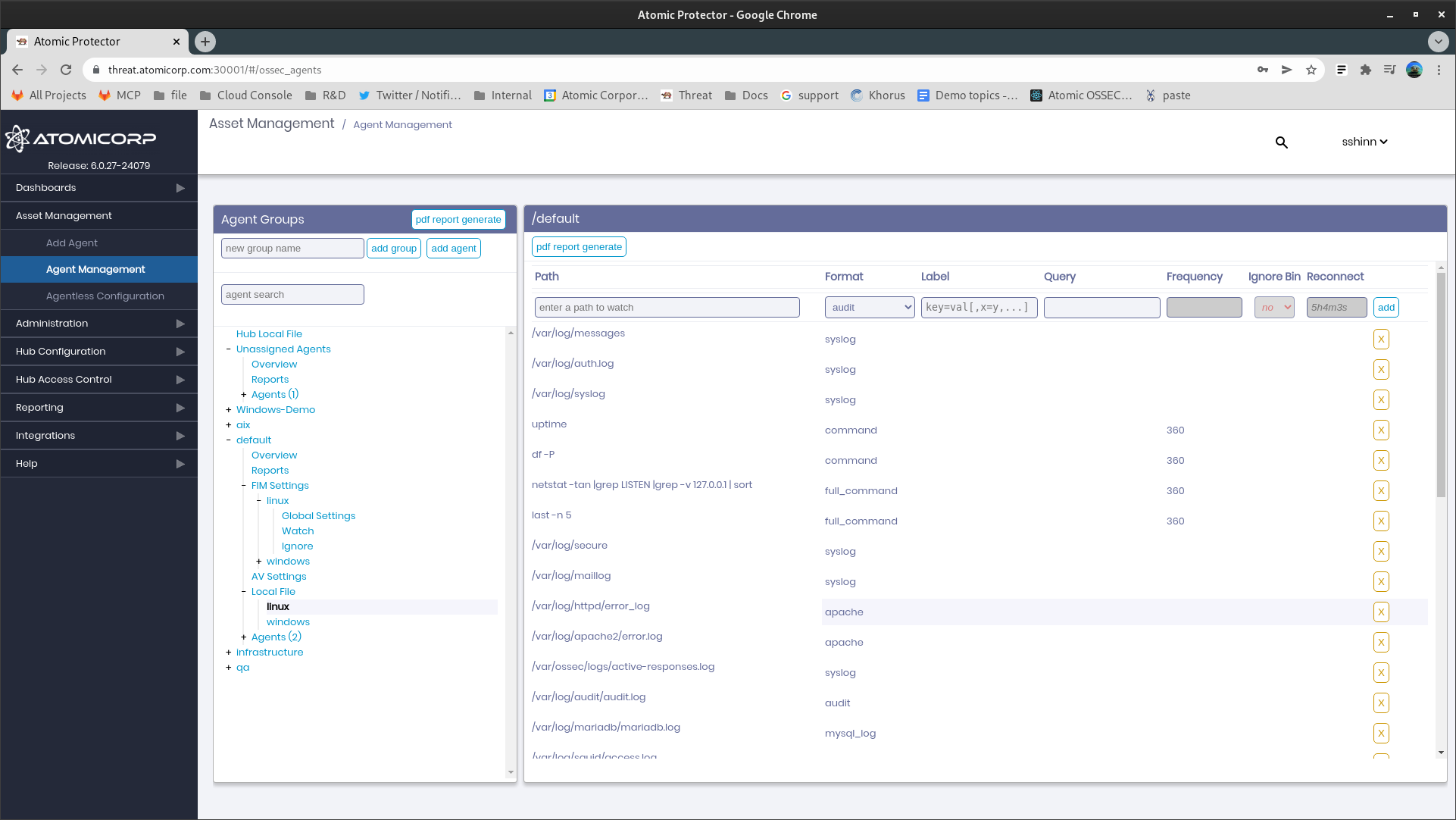
2.1 Path
Path to log file, or command to run. This value supports globbing on Linux, and can be combined with the IgnoreBin command to automatically exclude binary files when using the globbing option.
Note
When declaring paths, always use unix style /. Example: C:/exampledirectory
2.2 Format
Format of the log file type to use.
apache: Apache format logs
audit : Linux Audit logs
djb-multilog : Daniel J. Bernstein’s multilog output.
command: Used to run commands to generate log streams. Each line is treated as a separate event
Note
For security reasons, agents are configured to not accept commands from the server by default.This can be allowed in internal_options.conf
eventchannel: (Windows Only) used to declare a windows event channel combined with the Query option
eventlog: (Windows Only) legacy windows logging format on Windows XP, 2003 server, etc
full_command: Used to run commands to generate log streams. The full output is counted as a single event.
Note
For security reasons, agents are configured to not accept commands from the server by default.This can be allowed in internal_options.conf
iis: (Windows Only) Microsoft IIS web server
multiline: This format type is for log messages consisting of multiple lines. The number of lines used per message should be the same, and the number of lines should be specified
mysql_log: Mysql log format
nmapg: Nmap’s grepable log format.
postgresql_log: Postgresql’s log format
snort-fast: Snort’s fast text output format.
snort-full: Snort’s full text output format.
squid: Squid’s log format
syslog: syslog is used for plain text files with one log message per line. The log messages do not have to be in a syslog format.
2.3 Label
Used to add a custom json key->value in alerts.json for log events from this path or command.
2.4 Query
Eventchannel Only, Microsoft Windows eventlog format, using the EventApi. This should allow OSSEC to monitor both Windows eventlogs and the more recent Applications and Services logs.
2.5 Frequency
Used with command and full_command, Specifies the time in seconds between each check.
2.6 Ignore Bin
Used with Path globbing only, this restricts log parsing to ASCII only files.
2.7 Reconnect
Eventchannel only, specifies the time to wait before attempting to re-connect to the windows event channel
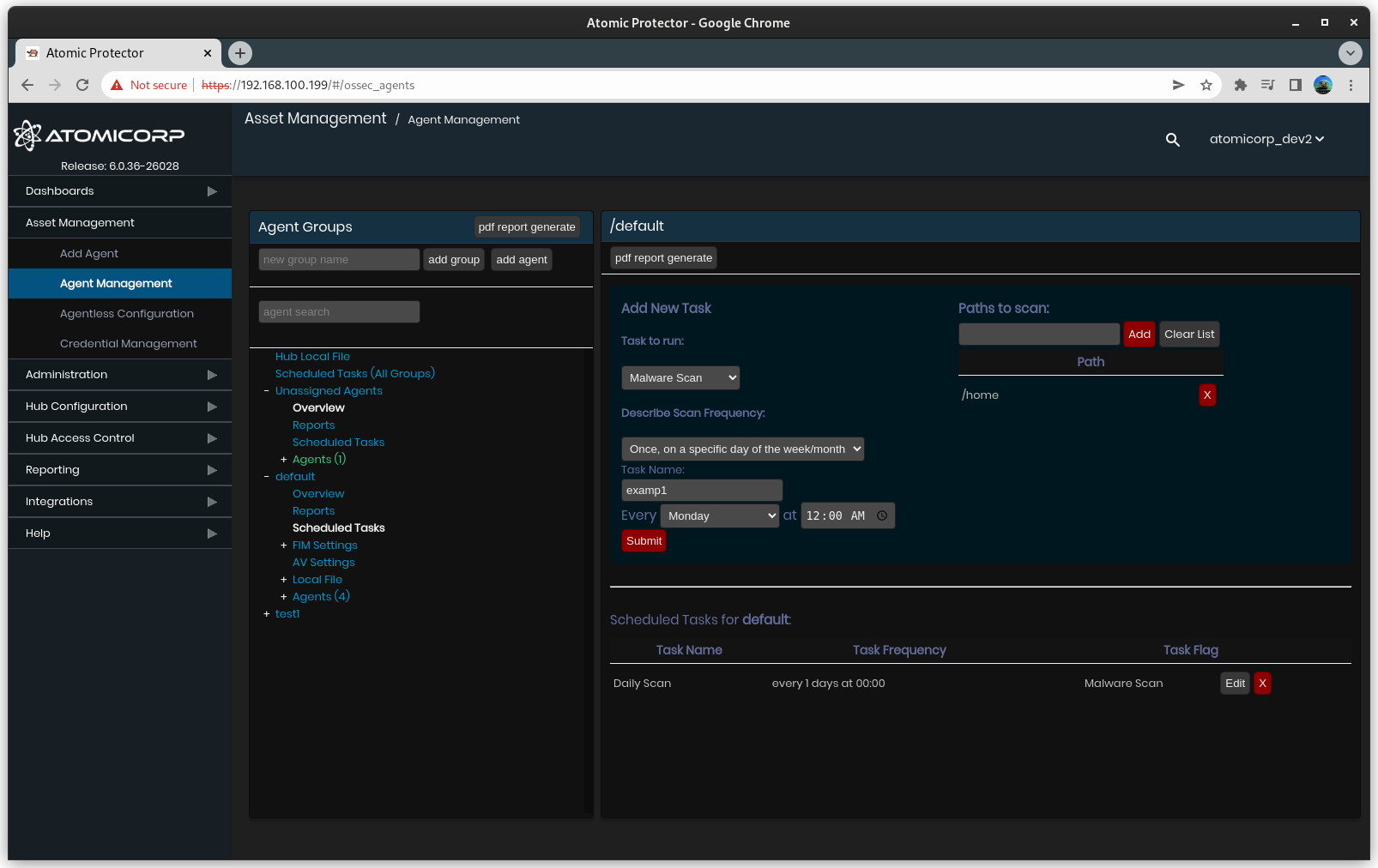
3.0 Scheduled Tasks: Malware Scan
The Atomic OSSEC task scheduler can be configured to automatically run scans, or generate reports globally, or at the group level.
Requires
Atomic OSSEC agent 4.4.3 and above
Clamav installation (available from the hub repo on RHEL/Centos/Rocky/AIX)
Step 1: Configure Scan
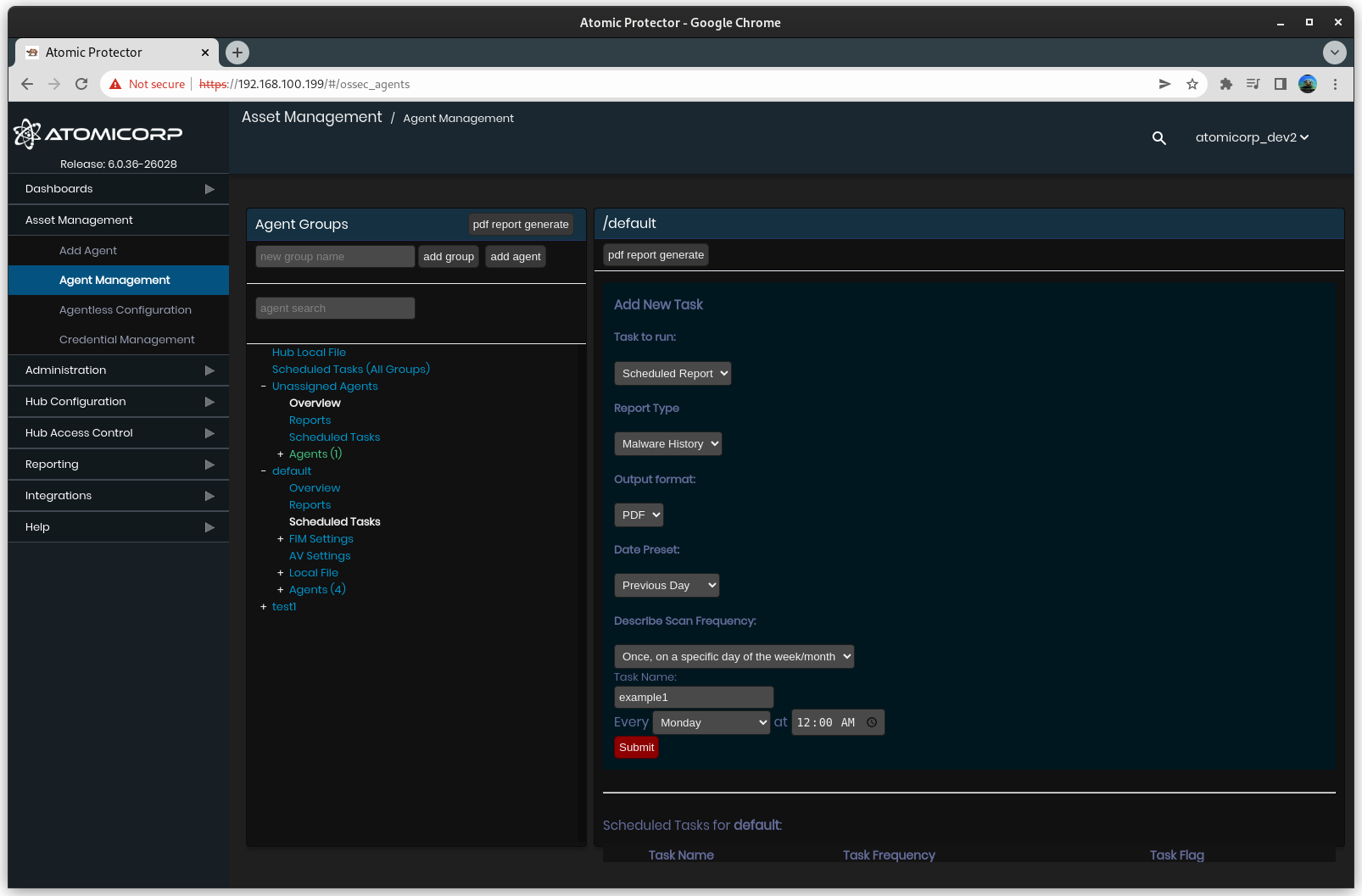
4.0 Scheduled Tasks: Malware Report
For scans configured in section 3.0, PDF reports can be generated on a defined schedule.
Requires
Scans configured in section 3.0
Step 1: Configure report
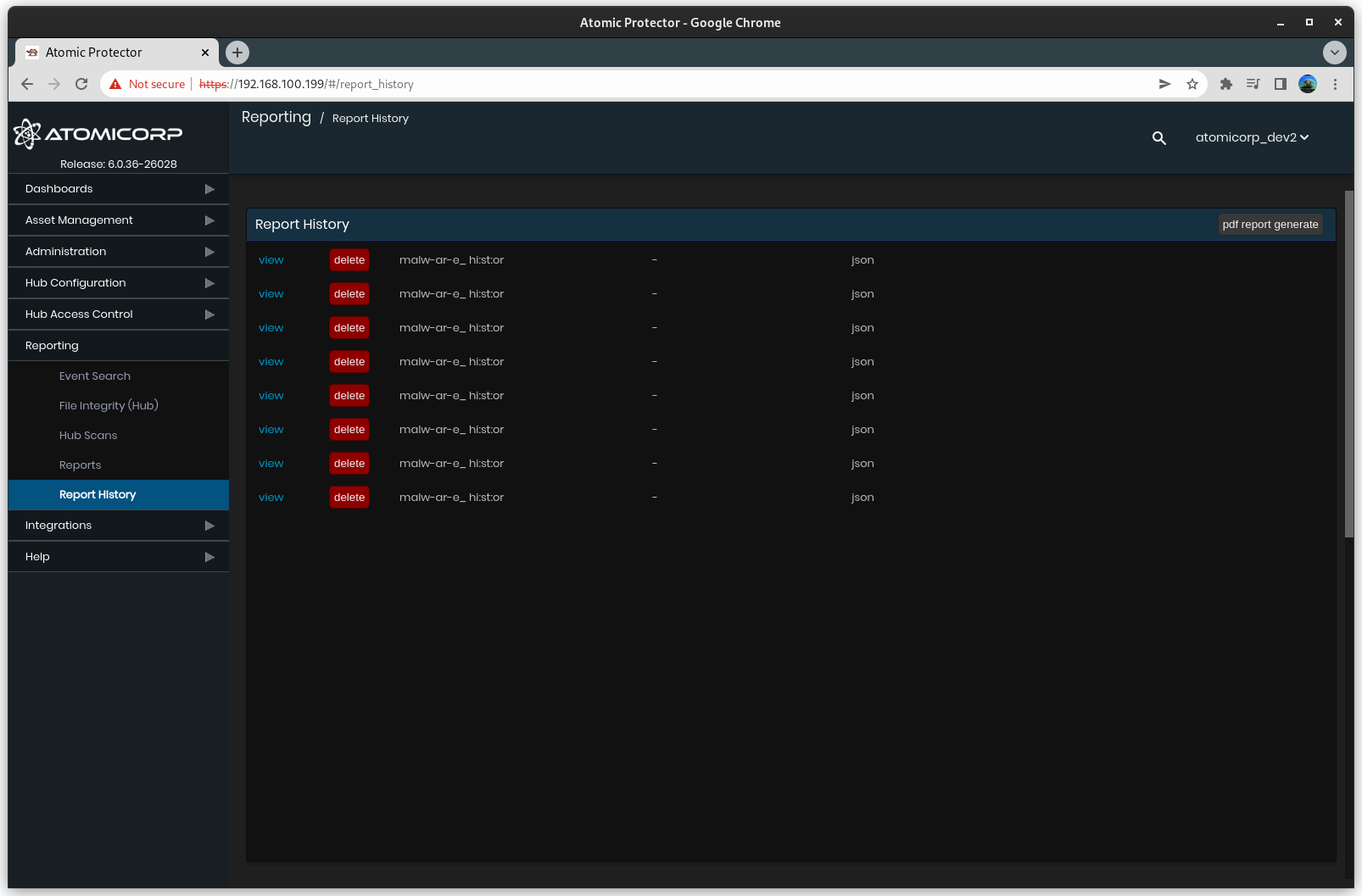
Step 2: Download Report
Can be found under Reporting->Report History
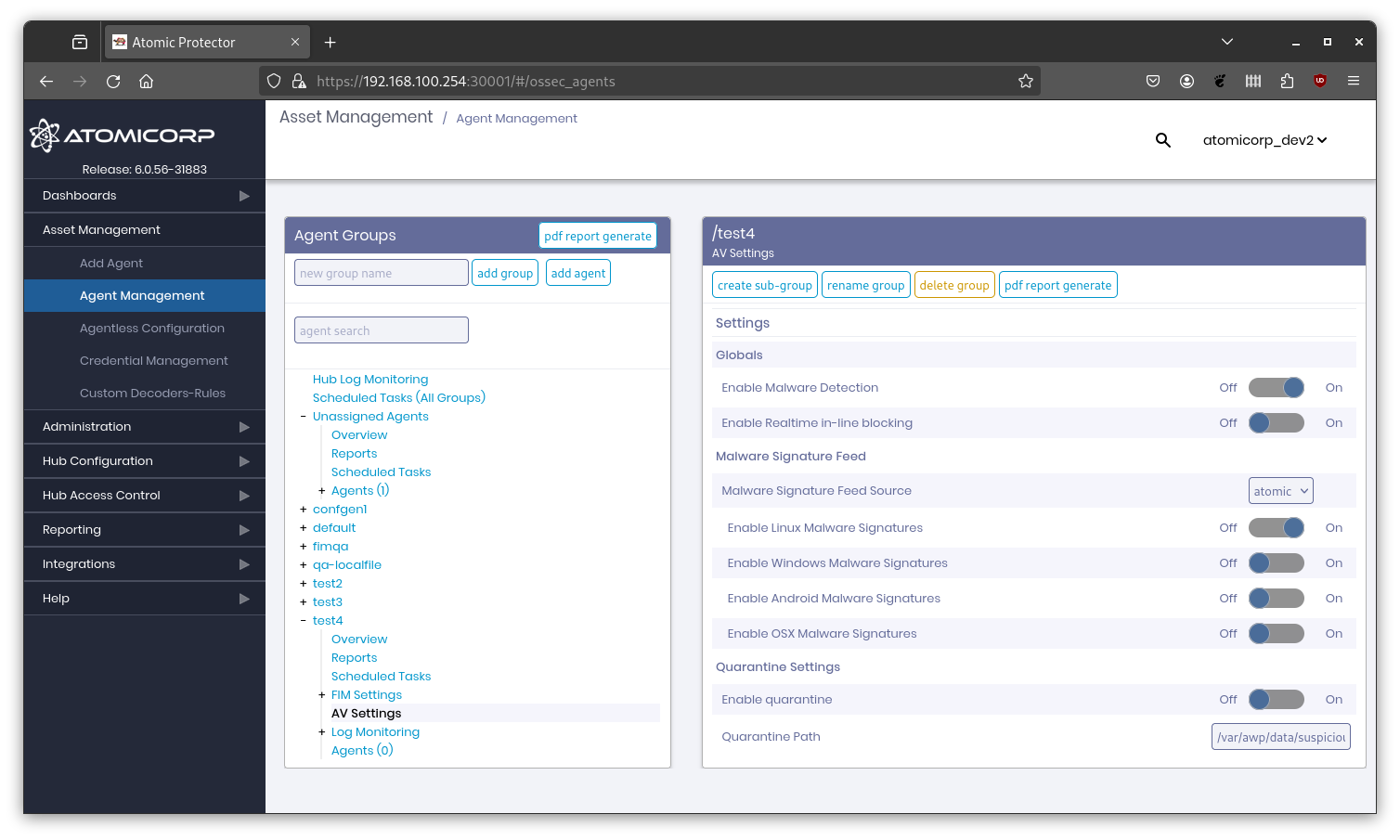
5.0 AV Settings
Atomic OSSEC supports central management for ClamAV for Anti-Virus scanning on Linux. This feature is not available on Windows.
Supported Platforms
Amazon Linux 2/2023
Centos 7
RHEL 7/8/9
Rocky Linux 8/9
Ubuntu 20/22/24
Debian 11/12
Note
Other RHEL clone platforms may be supported, but are not tested
Requires
The following are endpoint erquirements
Atomic OSSEC agent 4.6.0 and above
AWP-Agent 1.7 and above
Clamav 1.0 and above
Features
Real-time preventon of Malware
Reduced memory footprint over default clamav
Centralized management of Clamav settings
Centralized management of Clamav signatures
DLP support for SSN and CC data
Quarantine support
Configuration
By default the Clamav service is disabled. To enable it, navigate to the AV Settings tab and configure the following options, and click the Save button. This also applies when creating new asset groups.
Note
By default Clamav is DISABLED. It will not be activated until you click the Save button
Enable Malware detection: Enables/disables clamav on the endpoint. If set to Off, the clamd service will be stopped
- Enable Realtime inline blocking: Enables/disables real-time blocking of files through the service clamonacc. When enabled, this will prevent users from being able to read, access or execute malicious files.
Note
This requires directories to be monitored. See Real-Time Path Includes below
Malware Feed Source: Atomic, Hub or Official, this configures clamav on the endpoint to get signatures from the Atomic or Official Clamav servers, which requires network access to the internet. Hub type will download updates from the Atomic OSSEC hub server. [Default: Atomic]
Note
Choosing the Official feed will greatly increase the memory footprint of the clamd Services. The Hub repo mirror will be updated with the offline installer, or if the system has internet access, every 24 hours automatically
Enable Linux Malware Signatures: Enables/disables the use of the Linux Malware signatures. [Default: On]
Enable Windows Malware Signatures: Enables/disables the use of the Windows Malware signatures. [Default: Off]
Enable Android Malware Signatures: Enables/disables the use of the Android Malware signatures. [Default: Off]
Enable OSX Malware Signatures: Enables/disables the use of the MacOS Malware signatures. [Default: Off]
Enable Quarantine: Enables/disables the use of the Clamav quarantine. [Default: Off]
Quarantine Directory: The directory to store quarantined files. [Default: /var/awp/data/suspicious/]
DLP Structured Data Detection (CC, SSN): Enables/disables the detection of structured data such as credit card numbers and social security numbers. [Default: Off]
DLP Minimum Credit Card Threshold: The minimum number of credit card numbers to trigger an alert. [Default: 3]
DLP Detect Credit Card numbers only (exclude Debit/Private label Cards): Enables/disables the detection of credit card numbers only. [Default: Off]
DLP Minimum SSN Threshold: The minimum number of social security numbers to trigger an alert. [Default: 3]
DLP Detect SSN format xxx-yy-zzzz only: Enables/disables the detection of social security numbers in the format xxx-yy-zzzz only. [Default: Off]
Real-Time Path Incudes
Paths to monitor for real-time blocking. This requires both Malare detection and Realtime inline blocking to be enabled. Once enabled a monitored directory will be protected from malware.
Note
Some Clamav versions having no directories configured for real time blocking will result in the clamonacc service not starting. This is expected behavior
Real-Time: User Excludes
Users defined here will be excluded from malware detection. This is useful for users that are performing forensic activities, services involved in malware analysis, or privileged users such as root.
Architecture and Workflow
Once enabled from the Hub Server, the agents will download this latest configuration and trigger
/var/ossec/bin/ossec-control restart
control will call /var/ossec/modules/clamav/clam-module.sh
clam-module.sh will load its configuration from /var/ossec/etc/shared/malware-detection
clam-module will configure clamd.conf or clamd@scan.conf on the system, and freshclam
clam-module will trigger /var/ossec/modules/clamav/freshclam to download updates
Clamd will be (re)started if enabled
clamonacc will be (re)started if enabled